Last updated on July 7th, 2024 at 10:49 am
Phishing emails are still and thing, and still ripping off our most vulnerable citizens.

Image by Muhammad Ribkhan from Pixabay
This post is a guest submission. Please see our Affiliate Disclosure & Notification for details.
This post may contain affiliate links. We may earn a commission if you purchase an item through our links. It costs you nothing and helps us to fund this blog. Please see our Affiliate Disclosure & Notification for details.
Phishing is a form of cybercrime. These cybercriminals contact their victims via email or text messages on the phone, and they pose as legitimate institutions, so the victim doesn’t get suspicious. The victim is lured into providing confidential information like personal identity information, passwords, and banking or credit card details. Important accounts are then accessed by these criminals using this information, which can result in financial loss and identity theft. That can be especially detrimental to small businesses.
Phishing emails have some common features:
- Too good to be true: People’s attention is grabbed immediately by offers and statements that are designed to appear lucrative and eye-catching. This could be a claim that you won something like a lottery, an iPhone, or some other prize that will make the victim eager to claim the prize. The moment that person clicks on the email, he or she becomes vulnerable. The saying “If it’s too good to be true, it probably is” applies here.
- Sense of urgency: Creating a sense of urgency causes victims to think they might lose out on an incredible deal if they don’t act fast. The deal is usually available for a limited time only. You could also be told to update your personal information within the next few minutes to prevent your account from being suspended. Reliable institutions will usually not ask you via emails to update your personal information. Therefore, it’s good practice to contact your bank or institution you’re dealing with directly rather than clicking on any link in an email.
- Hyperlinks: A link in an email is not always what it seems to be. If you hover over a link, it’ll show the actual URL where you will be taken. The name might look fine, but there could just be a slight misspelling that you don’t pick up just by glancing over it. Look very carefully as an “r” and an “n” next to each other in that order can appear like an “m” (rn). If you don’t notice that, you can be directed to a different URL.
- Attachments: You shouldn’t open emails with attachments that you don’t expect or don’t make sense. Such an attachment could contain some malware or virus that can be harmful to your system. A .txt file is the only file type that is always safe to click on.
- Unusual sender: Any link in an email that looks slightly suspicious or out of the ordinary, whether it appears to be from someone you know or not, shouldn’t be clicked on.
Here are five of the most common ways you can be scammed through email.
Phishing Emails
As stated by the F-Secure report, phishing emails and malignant attachments sent to employees are usually where over 30% of security incidents start. Phishing is continually evolving and is a real and serious threat for users and organizations.
Phishing is communication via email or social media. In most cases, a user will receive an email from a cybercriminal who will lure them into revealing sensitive and confidential information. This could include banking details or login details for social media networks, cloud storage, or a work account.
To a user, it may appear that the email comes from an official source like the bank or another legitimate company, so they will not suspect anything. Social engineering techniques are then used to persuade a user to open a malicious link to a website that appears legit. This website, however, is controlled by cybercriminals and only mirrors the real one.
The criminal creates a sense of urgency by convincing a user that their account is under attack and that they need to confirm their identity to save the account from being locked down. This usually causes panic, especially when the victim is busy and acts without thinking clearly.
Below is an example of a scam email making the rounds:

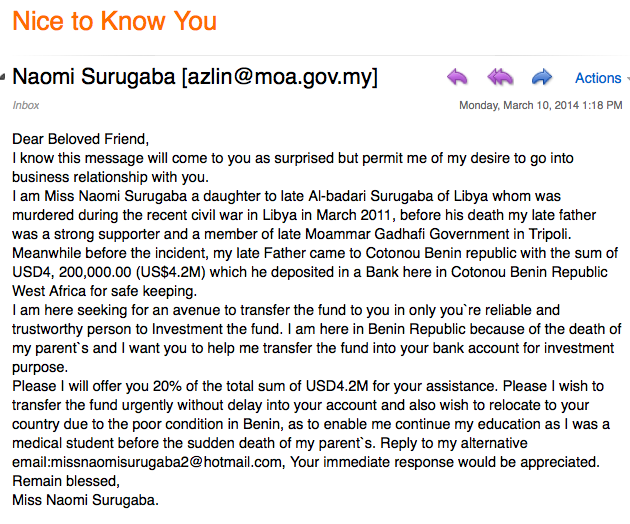
The Nigerian Scam
The Nigerian scam is probably the most popular and oldest scam used on the internet, usually by a member of a wealthy Nigerian family, tricking people from all walks of life. The scam is named after a section of the Nigerian Criminal Code and is known as the 419 fraud.
This particular scam starts with someone receiving an emotional email from the scammer. The scammer is usually a woman and poses as a government official, businesswoman, or a member of a very wealthy family. She then asks you to help her withdraw a very large sum of money, which can be an inheritance, from a bank account. By doing so, you need to pay an initial fee or fees for the documents. You are also offered a percentage of the amount for your help, and this percentage is usually a huge amount of money.
That is the hook, and once you start paying these fees, they will persistently ask you for more money for additional services like transaction costs. To make it all look real, you will even receive documents about the process, but the reality is that it’s a scam. You are left broke and without any of the promised money.
Here is an example of a Nigerian scam:
Greeting Card Scams
We all get a greeting card of some kind in our email inbox at some point, and it seems to come from a friend of someone we care about. The greeting card is another old scam that downloads malicious malware onto your computer’s operating system the moment you open the email and click on the card. The malware can cause annoying pop-ups with ads to appear on the screen.
The malware is dangerous, and once it’s installed onto your system, your computer becomes a bot in a network of infected computers. It starts sending your private data and financial information to a fraudulent server under the control of these criminals.
Here is an example of such a greeting card:

Lottery Scam
This scam comes in the form of an email informing you that you have won a large sum of money from playing the lottery. You will, however, need to pay some fees to get your prize. That in itself should be a warning, but what are a few hundred dollars compared to hundreds of thousands or even a million dollars you will get, right? You don’t even care if you can’t remember buying those lottery tickets.
One usually gets drawn into a fantasy world we all dream about, like quitting our jobs and never needing to work again or buying that dream car or a house. Our imagination easily falls prey to these amazing scenarios.
The dream, however, gets shattered the moment you come back to reality and realize you have been scammed. Do you perhaps recognize this kind of email? Maybe you’ve seen one at some point in your inbox:

Survey Scam
This scam looks quite innocent and is very common. At some point, we all express some interest in something on the internet. So if you receive an email regarding one of those interests, asking you to complete a survey on such interest, you might think it’s harmless to participate. However, this email is spam, unless you specifically requested to be on their mailing list, so you shouldn’t even open it.
The moment you open the link to the survey, malignant software gets downloaded and installed onto your computer. Through this software, cybercriminals can track all your movements on your computer and then collect all your confidential information like your passwords and banking details. You won’t be aware of it until it’s too late. That is usually when you start seeing charges on your credit card for purchases you haven’t made. This is identity theft, and your life can be ruined by it, so be careful.
Conclusion
The bottom line is that the internet is not a very secure place, and you should keep your personal information protected at all times. These attackers or scammers are constantly improving their knowledge and skill to hack into seemingly secure systems. That is their job, just like you have your day job. They make a living from committing a crime, so they need their skills and knowledge to be topnotch to keep up with the technological advancements.
Without a doubt, many of us have come across a few of these scams. Scammers know how to trick people, so if you see anything in your inbox that doesn’t seem right, get out of there for your sake.
Kirk is a writer who specializes in dissemination of cyber security information & news.

Subscribe to Our Mailing List
If you found the information in this post helpful, we'd love to have you join our mailing list. We promise we won't spam you, we only send out emails once a month or less.