Last updated on July 7th, 2024 at 10:48 am
If you need a high-level view of where security holes frequently live, this is it.

This post is a guest submission. Please see our Affiliate Disclosure & Notification for details.
This post may contain affiliate links. We may earn a commission if you purchase an item through our links. It costs you nothing and helps us to fund this blog. Please see our Affiliate Disclosure & Notification for details.
- Why Web Security Matters?
- Top 10 Security Flaws and How to Fix Them
- Backdoor #1: Injection Flaws
- Backdoor #2: Broken Authentication
- Backdoor #3: Сross Site Scripting
- Backdoor #4: Insecure Direct Object References
- Backdoor #5: Misconfigurations
- Backdoor #6: Data Exposure
- Backdoor #7: Missing Function Level Access Control
- Backdoor #8: Cross Site Request Forgery
- Backdoor #9: Outdated Software
- Backdoor #10: Unvalidated Redirects
- Best Security Testing Tools
- Wrapping Up
You can be completely sure that your site is an impregnable fortress for intruders, but world statistics suggest otherwise. According to patchstack, more than 30,000 websites are hacked every day in the world. These horrific numbers prompt website owners to take action to ensure your site is as secure as possible, and in this article, we’ll share ten web vulnerabilities and how to fix them. Without further ado, let’s get started.
Why Web Security Matters?
Protecting your website should always come first, regardless of the site’s subject matter, whether it’s online learning, news bulletins, or an entertainment site with cartoons for kids. Here are some of the most important reasons why you should protect your website as much as possible:
- You protect yourself from various viruses and malware
- You protect users’ personal data from various phishing programs
- You attract more visitors and new users due to the fact that your site is secure
- You rank higher in search engines
- You protect your personal data from theft
Now, let’s talk about the most vital part of our article – security backdoors and ways to fix them.
Top 10 Security Flaws and How to Fix Them
We have collected 10 of the most important security problems and talked with web security experts to find out the necessary preventive methods to avoid such security errors.
Backdoor #1: Injection Flaws
In simple terms, this kind of hack involves a web form field or URL string parameters. An attacker injects malicious code that can modify tables, delete important information, and much more. These flaws can exist in contact forms, login pages, checkout pages – basically any page that contains a space where a user could enter information may be a target.
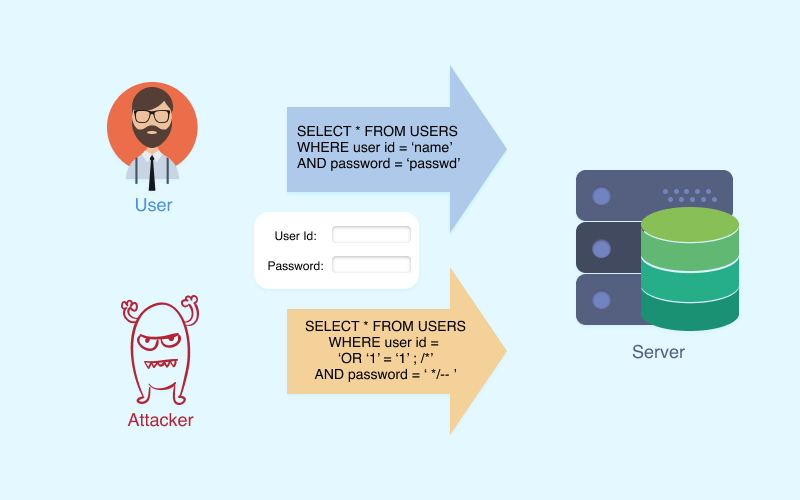
To protect your website against such attacks, you should rely on the input filtering that is in your framework (such as a web application firewall), since the effectiveness of such a method has already been proven and is an unspoken security standard.
Backdoor #2: Broken Authentication
This problem can be the cause of a single malfunction or a combination of many problems. For example, passwords cannot be encrypted during storage or during transmission, or session fixation might be possible. And these are just two of the many reasons.
In order to make authentication as secure as possible and prevent a huge number of problems, you should also use a framework. In addition, ensure all communication uses https rather than the non-secure http protocol.
Backdoor #3: Сross Site Scripting
If you do not go into technical details, during such attacks, an attacker launches malicious code into a site that can harm both your data and the data of site visitors.
The easiest way to protect yourself from such actions is not to return HTML tags to the user. This will protect your site from embedding HTML content that could harm your site.
Backdoor #4: Insecure Direct Object References
This is a fairly common vulnerability related to the insecure provision of internal objects (these can be database keys or a file). For example, a password reset works this way. During password reset (if there is a vulnerability), an attacker can change, for example, the username field in the URL and specify “admin” instead of his own.
The surest way to protect yourself is to store data inside and work with data without transferring it from the client through CGI parameters. You can use a variety of session variables that exist in many modern frameworks.
Backdoor #5: Misconfigurations
Another common cause of vulnerabilities is an incorrect configuration of web servers. And this is not surprising since there are many pitfalls in the setup. For example, you can use outdated software on the server or forget to change the default keys and passwords.
To eliminate such oversights, it is worth using an automated build and deployment process of the server with tests at the end of the deployment. They will help you identify errors and fix them early. For website owners, you’ll want to ensure you use a reputable hosting company to host your site.
Backdoor #6: Data Exposure
If important data is not encrypted in any way, this is the first bell that something is clearly wrong with your site. Any confidential data must be encrypted, and if you neglect it, you risk losing important data since it will not be difficult for attackers to steal it.

For maximum security, the first step is to use HTTPS along with reliable PFS. Do not accept any data over non-HTTPS connections. The second step will be encryption of all confidential data that you store on the server. And remember that all passwords must be hashed.
Backdoor #7: Missing Function Level Access Control
In simple terms, this is an authorization error when authorization was not performed when the function was called. For example, in the admin panel interface, the login button appears only if the user is really an administrator. An attacker can easily spoof the function, call the button and enter the admin panel.
The only way to avoid such cases is to perform authorization only on the server-side.
Backdoor #8: Cross Site Request Forgery
CSRF is the process when some other party cheats the browser and abuses its powers. For example, a third-party site could force a user’s browser to abuse its authority in order to do something for an attacker.
To avoid such a situation, it is worth using a hidden token that will be hidden in the form field and which will be inaccessible to a third-party site.
Backdoor #9: Outdated Software
The more outdated software you use, the higher the chances of being attacked by intruders. Every day, new ways of hacking and new ways to resist them are invented. That is why it is very important to use only the latest software and web development stack for your website.
For those WordPress folks out there, this also means ensuring your core, themes, and plugins are all running the latest versions and anything that has been abandoned by the developer should be removed from your site as soon as possible.
Backdoor #10: Unvalidated Redirects
This problem is related to redirects and which lend themselves to spoofing. For example, there is a GET parameter, and an attacker, manipulating it, can send users from your site to sites with malware.
The best options for preventing such cases are to remove redirects from your site completely or create a static list of possible redirects.
Best Security Testing Tools
In order to identify vulnerabilities in the early stages, you should use specialized software. It tests your site according to many criteria and marks possible vulnerabilities that require immediate elimination. We want to highlight three great website validation tools.
- Netsparker. This program is ideal for testing SQL injections, and XSS comes with a free trial version.
- OpenVAS. One of the most popular programs on the market that is suitable for deep scanning and removing all possible vulnerabilities of your site.
- Acunetix. In addition to standard scanning for web vulnerabilities, this program can detect various errors in scripts in languages such as PHP, ASP.NET, and ASP.
Wrapping Up
These were the ten most common web vulnerabilities that you can encounter while building your website. And as you can see, these vulnerabilities affect different aspects of the site, and it’s very easy to miss one of them. But now, you are armed with knowledge and know exactly where to look for vulnerabilities and how to fix them.

Subscribe to Our Mailing List
If you found the information in this post helpful, we'd love to have you join our mailing list. We promise we won't spam you, we only send out emails once a month or less.